Startup marketing, billing, pricing, AI monetization by Arnon Shimoni
-
2020 is here! Why are we still using 1980s tech?
Before COVID-19 hit in full force, I went to Warsaw for the Big Data Tech show to give a short 15 minute talk. For your viewing pleasure, here it is! Slides are available on SlideShare It's 2020 – Why are we still using 1980s technology? from Arnon Shimoni
-
Your DBMS is slow. What do you do?
I first used SQL for an online blogging platform I was building in Perl back in 1999. Moving from a flat-file to MySQL was truly a lifechanging experience. The (then) four-year-old DBMS had a nice little set of features and optimizations that I could easily apply and get a decent performance boost. Call me a…
-
My top 5 “product” books
I will admit I don’t read enough. I find it hard to focus on stories after spending my work-day reading things rapid-fire. Most of my day is spent reading industry reports, e-mails, Slack messages, product requirements, tweets, etc. However, ny recent shift towards being a better product manager has lead me to really dig my…
-
Speaking at Data Innovation Summit and Big Data Warsaw
I’m kicking off 2020 by attending and speaking at both Data Innovation Summit and Big Data Warsaw. My talk titles are roughly around the idea of “It’s 2020 – why are we still using 1980’s tech?“ Big Data Warsaw is a tightly packed, quick-pace one-day event on February 27th in Warsaw, Poland Data Innovation Summit…
-
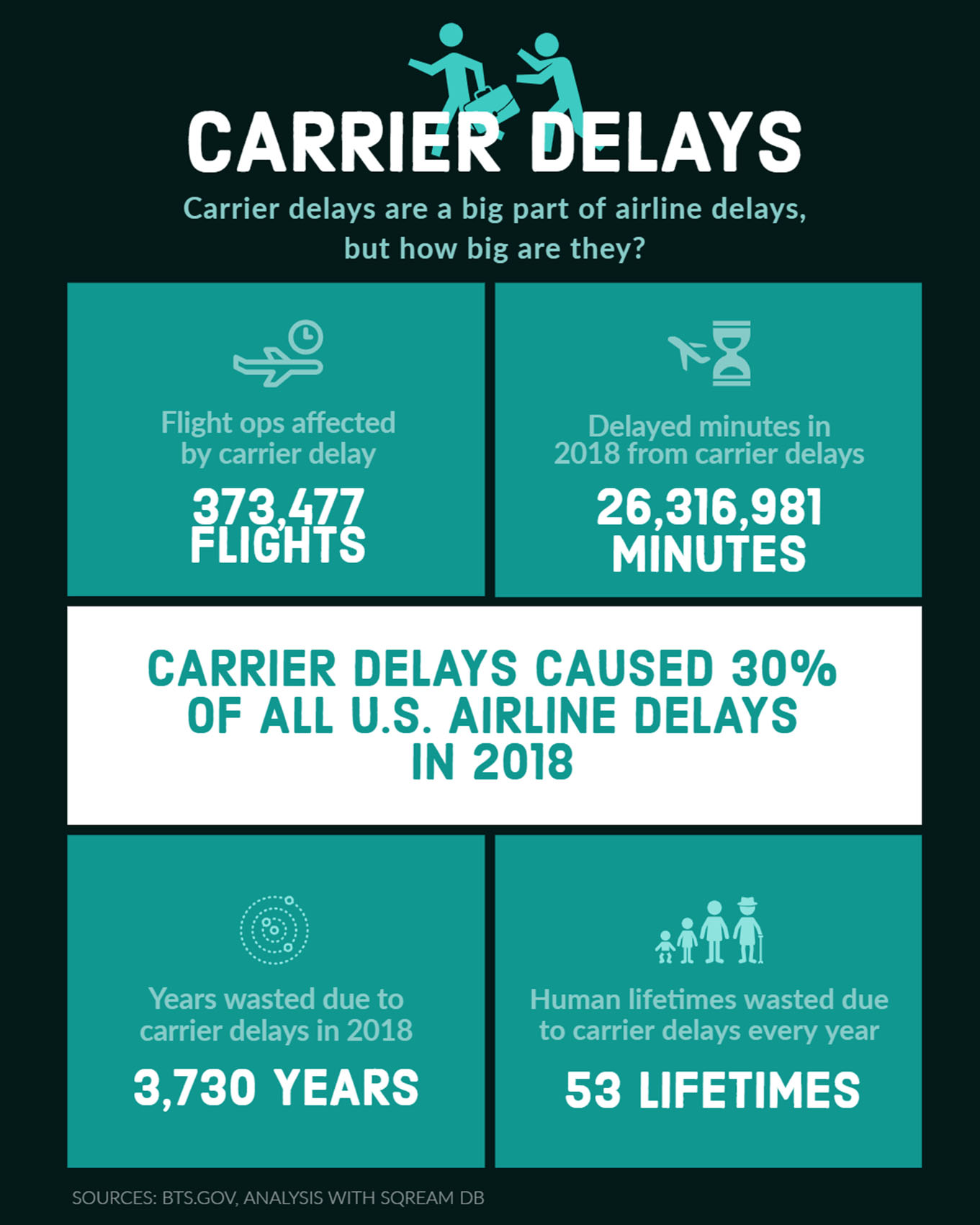
How airlines use your personal data to reduce delays – and why you should let them have it
Hundreds of articles have been written about how airlines track customers to upsell them, offer upgrades, personalize offers, increase loyalty, and even improve baggage tracking. However, one of the most interesting fields of airline operations is adapting to irregular operations – meaning using a combination of customer profiles, weather, route information, airport performance and more…
-
Another month, two more trade-shows under my belt
June is usually a fairly quiet month. However, this June I participated in two trade-shows. BDA Frankfurt by Whitehall Media was the first. It’s a very focused, one-day event that brings together data experts from Germany, Italy, France, the UK, Austria, Switzerland, and more. I got the opportunity to speak at this event about the…
-
I spoke at Data Innovation Stockholm
Despite living close by in Copenhagen, I mostly attend trade shows and expos in the US and far east. When I was given the opportunity to speak at Data Innovation Stockholm, I was excited because I’ve never had a chance to try out my content on a mostly European audience. The show spanned two days…
-
Quickstart – Installing nvidia docker in one guide
I have been frustrated when trying to install nvidia-docker, because the guides are split over several documents. NVIDIA’s own documents tell you to go install Docker first, but don’t tell you how. For Ubuntu 16 and 18, here are all the steps you need, one by one:
-
SQream DB at CMU – How we approached building a GPU database
Earlier in October, Jake (SQream’s architect) and myself flew to Carnegie Mellon University in Pittsburgh to give a talk as part of their Hardware Accelerated Database lecture seminar. It was great fun, and we even got to speak to a bunch of research students on their research topics. They had great ideas, which I’m sure…
-
I built a GeoJSON to CSV parser in Python
The GeoJSON to CSV parser is intended to help classic relational databases handle GeoJSON datatypes. It’s very simple, and converts each Feature from the FeatureCollection into it’s properties and a longitude, latitude coordinates. Check it out on my GitHub